See our new blogs on this topic:
Is Your Information for Sale on the Dark Web?
Dark Web: Inside the Internet’s Underworld
A recent online post under the “Fraud” category of a Dark Web marketplace read as follows:
“High Balance [redacted bank name] Logins 30K-150K Available…I bring you freshly hacked [redacted bank name] Bank Account Logins. The accounts are notorious for having weak security.”
The individual who wrote this post has since been indicted on federal charges of bank fraud, access device fraud, and aggravated identity theft. In a public statement pertaining to the arrest, FBI Special Agent in Charge of the Atlanta Field Office, Britt Johnson, stated that “The threat posed by cyber criminals is a persistently increasing problem for everyday citizens here in the U.S. and abroad.”
According to Silvino Schlickmann, INTERPOL’s Assistant Director of Research and Innovation, “Darknets are fast emerging as the preferred trading venue for organized crime networks and individuals to carry out illicit activities, with cryptocurrencies the preferred medium for paying for these criminal services.”
With this current reality as the backdrop, I thought it would be worthwhile to share some details from the above noted U.S. court case.
Overview of the Scheme
The Defendant allegedly advertised criminal services on a dark web marketplace and devised a scheme to defraud by which he would sell hacked bank account information on the dark market’s website.
The Defendant’s purpose in selling this stolen bank account information was to assist his dark market customers in obtaining unauthorized access to bank accounts so they could obtain money, funds, credits, and assets that were under the custody and control of a U.S. based bank and defraud that bank by falsely and fraudulently posing as its customers.
Sales Listings Categories — Fraud; Counterfeit Items; Carded Items; Drugs & Chemicals; Weapons
The indictment indicated that the marketplace website contained a number of features designed to assist prospective buyers who wished to purchase criminal services. For example, the marketplace sales listings contained categories corresponding to various types of criminal services. Categories included “Fraud,” “Drugs & Chemicals,” “Counterfeit Items,” “Weapons,” and “Carded Items.” The website also had a search functionality that allowed users to search for items by name, and similar to big brand sites like Amazon.com and eBay.com, users of the website can rate sellers and search for certain sellers by name.
The indictment also stated that “customers that want to buy goods or services on [redacted marketplace name] must use a virtual cryptocurrency known as Bitcoin.”
U.S. Bank Customer Information — Usernames, Passwords, Physical Addresses, Email Addresses, Telephone Numbers, and Bank Account Numbers
In early May 2016, the Defendant advertised the sale of stolen bank account information on the dark web marketplace under the “Fraud” category. In a listing titled “High Balance [redacted bank name] Logins 30K-150K Available,” he used his online nickname and wrote “I bring you freshly hacked [redacted bank name] Bank Account Logins. The accounts are notorious for having weak security.” The listing identified the sales price as $66.99 USD and indicated that the Defendant had sold 11 of the high-balance account logins since November 11, 2015.
In mid-March 2016, the Defendant advertised the sale of “Hacked [redacted bank name] Bank Account Logins $100-$500 Balances.” The listing indicated that the sales price was $9.99 USD, that he had sold 32 since November 5, 2015, and noted that “[t]his listing is for active [redacted bank name] bank account balances of $100-$500.”
A review by U.S. law enforcement of information purchased from the Defendant on this dark web market confirmed that it contained usernames, passwords, physical addresses, email addresses, telephone numbers, and bank account numbers belonging to a U.S. bank’s customers.
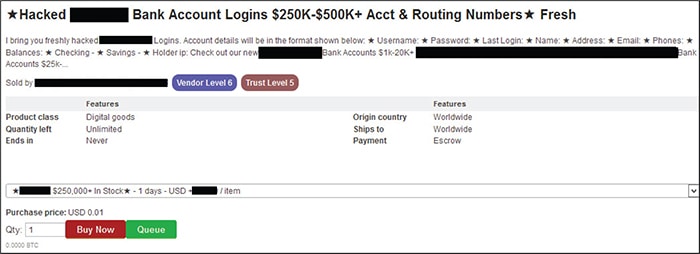
The sample screen shot below is from the same marketplace as the one identified in the indictment.
Two Cybercrime Classifications: Cyber Intrusions and Cyber-Enabled Crimes
Law enforcement has indicated that cybercrime is a fast-growing area of crime with more and more criminals exploiting the speed, convenience and anonymity of the Internet to commit a diverse range of criminal activities. Law enforcement generally makes a distinction between two main categories of cybercrime: cyber intrusions and cyber-enabled crimes.
Cyber intrusions include attacks against computer hardware and software such as spear phishing; malware; password attacks; and SEO attacks.
Cyber-enabled crimes encompass a wide range of financial crimes such as account take-over; business e-mail compromise; ransomware; romance scams; advance fee lottery schemes; credit/debit/ATM card fraud; theft of PII; point of sale breaches; false tax return filings; elder abuse; etc. and can also include crimes against children and terrorism.
Business e-mail compromise (BEC) is an example of a cyber-enabled fraud which targets businesses that has recently seen explosive growth. BEC is defined as “a sophisticated scam targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments. The scam is carried out by compromising legitimate business e-mail accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.”
In mid-June 2016, the FBI issued an alert stating that the BEC scam was continuing to grow, evolve, and target businesses of all sizes. The advisory reported:
- 1,300% increase in identified exposed losses since January 2015
- victims in all 50 states and 100 countries
- $3.1 billion worldwide exposed dollar loss (actual and attempted loss in USD)
FinCEN “Advisory to Financial Institutions on E-Mail Compromise Fraud Schemes” (FIN-2016-A003)
I would highly recommend that all financial institutions read the very informative advisory on e-mail compromise fraud schemes which FinCEN published on September 6, 2016. The advisory explains how Business E-mail Compromise (targets commercial accounts) and E-mail Account Compromise (targets personal accounts) schemes work. It outlines various scenarios for both Business E-mail Compromise (BEC) and E-mail Account Compromise (EAC) schemes and provides a comprehensive list of BEC and EAC Fraud Red Flags which were developed in consultation with the Federal Bureau of Investigation (FBI) and the U.S. Secret Service (USSS). The advisory “Advisory to Financial Institutions on E-Mail Compromise Fraud Schemes” (FIN-2016-A003) is available on FinCEN’s website.[/vc_column_text][/vc_column][/vc_row]