ACH payments have become one of the primary means of noncash payment in the past fifteen years. As consumers demand more convenience and flexibility in their banking options — these popular electronic money transfers create potential risks for your financial institution.
The 2016 Federal Reserve Payments Study shows a significant growth in ACH payments simultaneous with a continuing decline in check payments. Estimations in the report indicate that total ACH payments have grown at an annual rate of 4.9% (volume) and 4.0% (value) since 2012.
The study shows that ACH payments make up a significant portion of the value distribution of core non-cash payments.
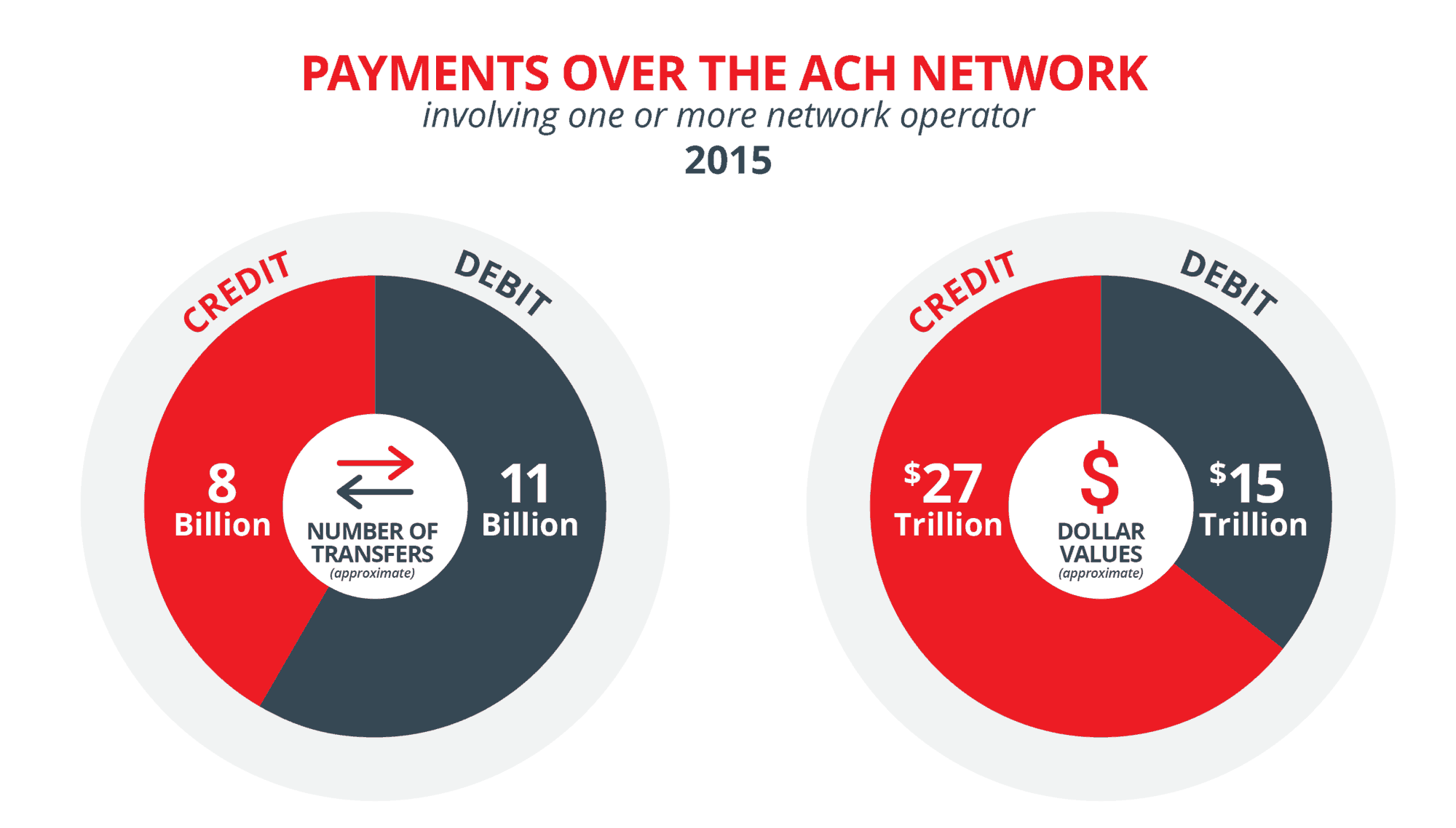
- Payments over the ACH network, involving one or more network operator, in 2015: 11.3 billion ACH debit transfers (dollar value: $14.86 trillion) and 8.0 billion ACH credit transfers (dollar value: $26.78 trillion) in 2015.
In April 2017, NACHA announced that the overall dollar value volume across the ACH Network in 2016 totaled $43.7 trillion, a 5.1% increase over 2015.
Ongoing risks
With same day ACH credits already available (September 2016) and same day ACH debits available in September 2017, it is reasonable to expect an increased workload for fraud investigators attempting to prevent ACH fraud — an expectation echoed throughout the industry. With a more narrow window for settlement than ever before — how will there be adequate time and resources to review and investigate these potential risks?
At the 2016 NACHA Payments Conference in Phoenix, Arizona, TD Bank conducted a survey of finance professionals. From a total of 283 responses, nearly 89% felt payments fraud would become a bigger threat to the industry in the next 2-3 years.
The 2017 Association for Financial Professionals Payments Fraud and Control Survey shows a continued upward trend of organizations victimized by payments fraud. In 2016, 30% of organizations were victims of ACH debit fraud and 84% of organizations experienced between one and five ACH fraud incidents.
Fraudulent ACH debits have already grown to such a degree that in March CUNA Mutual Group, an insurance company providing financial services to cooperatives and credit unions, published a risk alert warning to its members detailing the problem.
The alert referenced specific cases where members of several California-based credit unions recently initiated ACH debits against a county treasurer’s tax account at a bank, with some using the illicitly obtained funds to pay off vehicle loans.
How ACH fraud happens
There are many ways a criminal can perpetrate ACH fraud. Generally, they need control of a banking account to manipulate payments from, or debits against, the account. This control can be achieved through numerous different methods, such as opening new accounts with stolen identities to perform fraudulent A2A or P2P transfers, or executing online account takeover via the installation of malware on a victim’s computer.
In the case of online account takeover using email phishing techniques, victims unknowingly install malware that gives criminals access to online banking login credentials. Once they have access to the account, the criminals create ACH payments to new recipients — often accounts belonging to money mules paid by the criminals, who then, as instructed, transfer the illicit funds overseas or withdraw the money.
To ensure their fraudulent ACH payments go undetected, criminals may change the compromised account’s contact information. If the bank attempts to contact their customer about an abnormal ACH payment, they are actually contacting someone within the criminal’s network, who is all too happy to confirm the “validity” of the payment.
Another example is Vendor Impersonation Fraud (VIF). With VIF a criminal will contact a business impersonating a legitimate vendor or contractor. In this scenario, public-sector companies are often targeted as their vendor information is often publicly available. They will request the update of their account information, providing a new account number and routing information. When the next invoice from the vendor is paid, the funds instead land in the fraudster’s account.
Mitigating the risk
In the 2014 report, Fighting ACH Fraud: An Industry Perspective, ACI Worldwide published a list of the key approaches used to combat ACH fraud by financial institutions:
- Authentication, Tokenization, and Account Maintenance: Ensuring that multi-factors are compared for authorization, and reviewing any account changes with the customer before granted access or finalizing transfers,
- Risk-based approach: Balancing the risks of potential losses with the activity — short-term, low-value regular payments are lower risk than large value infrequent transfers.
- Behavior-based analysis: Analyzing for unusual and out-of-pattern activity, particularly on corporate or business accounts.
- Transaction monitoring: Using transaction monitoring to develop deep demographic, historical, and peer profiled can “elevate the predictive nature of finding fraudulent activity.”
- Advanced Analytics: Deploying analytical models that use all available data within an institution — or consortium data across a shared network of institutions — can uncover patterns of behavior that might otherwise go overlooked.
Criminals will continue to recognize the growing potential within ACH fraud, especially as ACH payments begin to move at a faster pace — giving investigators less time to uncover suspicious activity. As a result, FIs need to ensure they have controls in place to deal with elevated levels of attack.
This was echoed by Jane Larimer, NACHA’s executive vice president of ACH Network Services, during a September 2016 interview at Bank Info Security discussing, in particular, the adoption of same day ACH. During the interview, Larimer discussed the need for FIs to adopt strong fraud controls, such as transaction monitoring and anomaly detection, as the industry moves toward faster ACH payments
“From a high-level perspective, my hope would be that fraud departments see the risk mitigants and the potential for increased fraud risk [posed by faster payments],” said Larimer.
5 Indicators of Unusual ACH Transfers
The following are things to consider when attempting to uncover ACH fraud at your institution:
- Transfers to a new account. Is the customer attempting to make a large payment to an account they have never paid before? It is also valuable to know if the receiving account has ever been used by anyone else at your institution.
- Unusual values. For example, if a customer has historically transferred less than $1500 but is now attempting a transfer for $5000, it requires investigation.
- How well you know the customer. How old is their account? New accounts are inherently riskier. What is their overall relationship with your institution? If this customer has an established relationship with your institution and carries multiple products there is less risk.
- Online account activity. It is important to determine if there was unusual activity within the customer’s online account activity, which may indicate a takeover. For example, has the person recently altered contact information or has the business recently altered payee information via their online account?
- Quick withdrawals. This one is closely related with the age of the account. Criminals will often open a new account, sometimes using a stolen identity, fund the account from another institution and then attempt to withdraw the funds before your institution has reviewed the ACH returns.
Death by a thousand cuts
ACH fraud might be described as “death by a thousand cuts.” A single fraudulent transfer may not come with an eye-watering loss but they can quickly add up to one.
As same-day ACH grows in popularity, the risks for institutions are obvious. The need for rigorous monitoring is greater now than ever before.
Learn how Verafin can help your institution by identifying emerging fraud trends, managing the challenges posed by faster payments, and protecting your customers from scam scenarios like BEC, with real-time monitoring for ACH Fraud.